Published to clients: February 10, 2026 ID: TBW2099
Published to Whisper Club: February 10, 2026
Analyst(s): Dr. Doreen Galli
Photojournalist(s): Dr. Doreen Galli
ABSTRACT
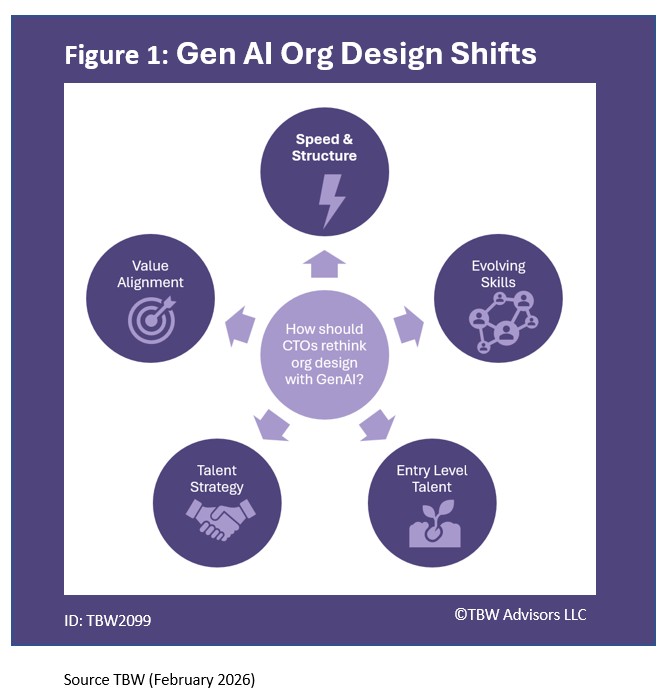
“This Whisper Report explores how CTOs should rethink organizational design in the world with Generative AI. Generative AI introduces structural shifts that accelerate delivery and reshape skills, workflows, and talent strategy. The research was conducted at HR Tech in Las Vegas. It highlights how agile cycles, cross‑functional skills, and HR collaboration strengthen organizational resilience.Quotes come from leaders at RChilli, Darwinbox, FitFirst, Fountain, FranklinCovey, Eightfold AI, Gem, and Aptia USA.”
Analysis available only to clients at this time. Join the YouTube Whisper Club at the Whisper Club Level to get access to the video edition today.
Related playlists and Publications
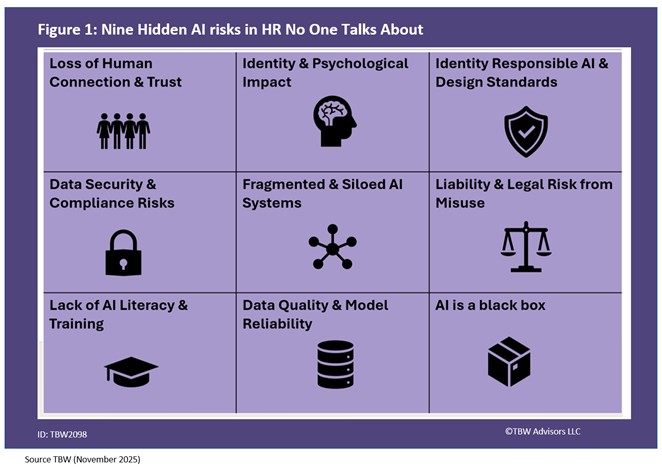
- Playlist for Whisper Report: What’s the biggest AI risk in HR no one talks about?
- Playlist for Whisper Report: How should CTOs rethink org design with GenAI?
- Playlist for Whisper Report: What HR tech trend will disrupt engineering hiring next?
- Conference Whispers: HR Tech 2025
Corporate Headquarters
2884 Grand Helios Way
Henderson, NV 89052
©2019-2026 TBW Advisors LLC. All rights reserved. TBW, Technical Business Whispers, Fact-based research and Advisory, Conference Whispers, Industry Whispers, Email Whispers, The Answer is always in the Whispers, Whisper Reports, Whisper Studies, Whisper Ranking, Whisper Club, Whispers, The Answer is always in the Whispers, and One Change a Month, are trademarks or registered trademarks of TBW Advisors LLC. This publication may not be reproduced or distributed in any form without TBW’s prior written permission. It consists of the opinions of TBW’s research organization which should not be construed as statements of fact. While the information contained in this publication has been obtained from sources believed to be reliable, TBW disclaims all warranties as to the accuracy, completeness or adequacy of such information. TBW does not provide legal or investment advice and its research should not be construed or used as such. Your access and use of this publication are governed by the TBW Usage Policy. TBW research is produced independently by its research organization without influence or input from a third party. For further information, see Fact-based research publications on our website for more details.