Las Vegas, NV August 2- August 7
Published to clients: August 11, 2025 ID: TBW2089
Published to readers: August 12, 2025
Published to Email Whispers: TBD
Public with video edition: TBD
Analyst(s): Dr. Doreen Galli
Photojournalist(s): D. Doreen Galli
Abstract:
After 61 videos including 4 first ever onsite livestreams, 150 minutes of recording including multiple exclusive shots – our coverage of Black Hat USA 2025 closes. Black Hat USA 2025 featured over 100 briefings and 120 sponsored sessions, with coverage spanning keynote presentations, technical sessions, and exhibit hall innovations. Topics ranged from AI-driven threat detection and agentic SOC platforms to identity verification and proactive risk management. Trends in cybersecurity regarding defence, use of AI agents, and focus on resiliency continue to grow.
Coverage on Computer Talk Radio August 2, and August 9.
The Conference
- Black Hat USA 2025 featured over one hundred briefings and 120 sponsored sessions. Attendance numbers are forthcoming. 2024’s edition featured over 20,000 in person attendees.
Cautions
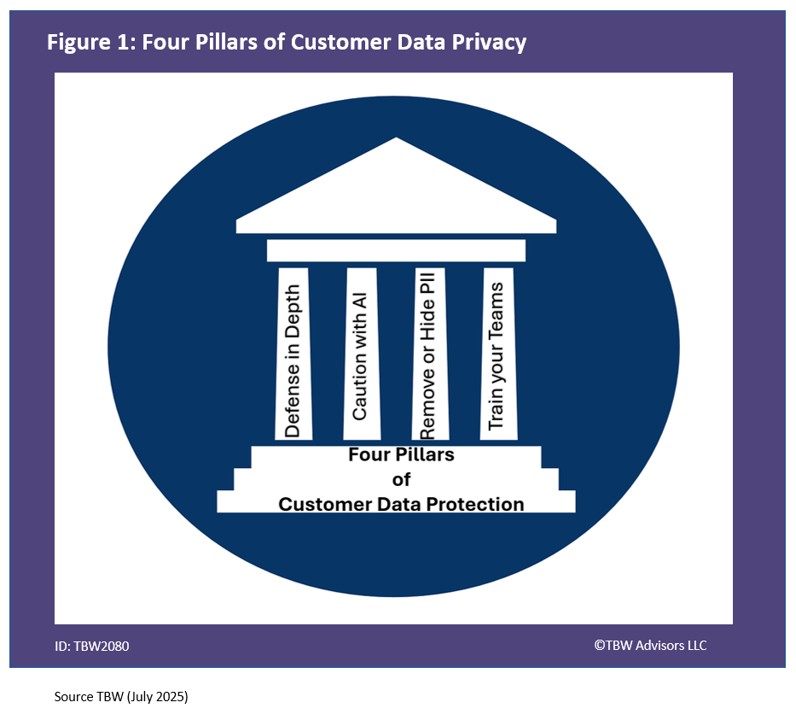
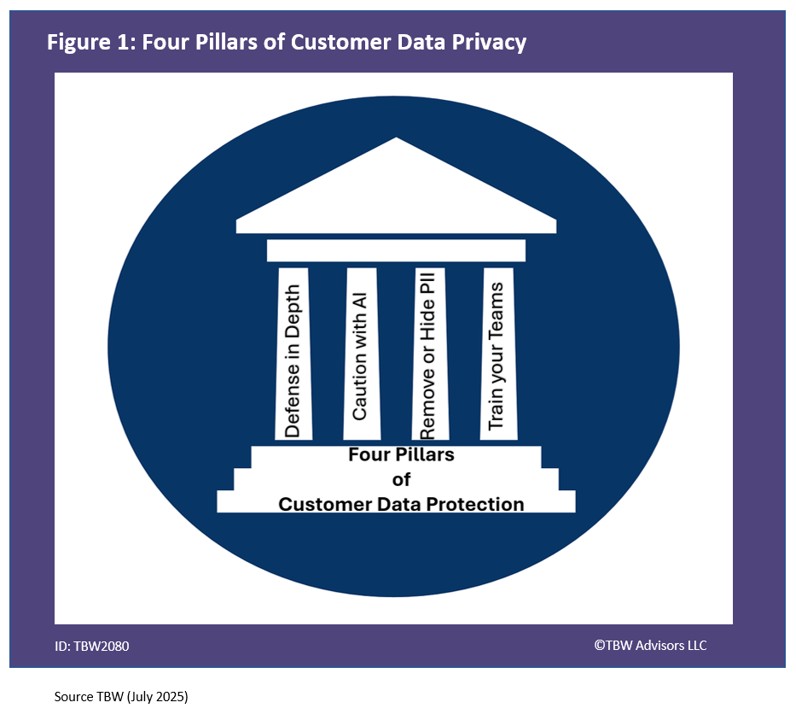
- Black hat is not a conference to attend without preparation. All of one’s technology should be up to date. One should ensure they are leveraging a VPN and a RDID wallet when intentionally going around black hat. If not using one’s phone, a portable faraday pouch is always beneficial.
- Friendly reminder: this research provides examples of what was shared with us at the event, not an evaluation, validation, or recommendation of the given technology.

Conference Vibe
After 61 videos and related fact checks, over 150 minutes of recording including for the first time ever – four onsite LIVESTREAMS – our coverage of Black Hat USA 2025 closes. Black Hat featured over one hundred briefings and 120 sponsored sessions. Clients may recall the expo hall restrictions during our coverage of HIMSS which treated the entire expo hall like a surgical operating room from a privacy perspective. Guess what? It was even tighter at Black Hat. Nonetheless, we were able to capture the energy as Expo Hall was opening. Not only that, for the first time ever, Informa (who owns Black Hat) gave permission to someone to do a walkabout in Expo Hall prior to its opening for the day. That’s right – enjoy your exclusive look at Black Hat USA 2025 Expo Hall. Not only that, we were able to capture the mouthwatering lunch served on Wednesday. Once again, unlike most events, the What’s To Eat? Video does not include any attendees enabling us to really get a great shot of the food! A first for TBW Advisors LLC – we did four livestreams while on site. One live stream on Tuesday, Wednesday, and Thursday morning. One final livestream went out on Thursday as I requested assistance on your favorite videos for my segment on the August 9th broadcast edition of Computer Talk Radio.
While at Black Hat USA 2025, we conducted research for three additional forthcoming Whisper Reports for our clients. The playlists are unlisted but available and will eventually fill in with the video version of the report so you may wish to bookmark these playlists.
- Whisper Report: What’s the biggest cybersecurity myth in 2025?
- Whisper Report: Can AI defend against AI-powered attacks?
- Whisper Report: What’s the next SolarWinds-level breach waiting to happen?
Readers and viewers wishing to experience the entire event are encouraged to view the Conference Whispers: Black Hat USA 2025 Playlist in its entirety. Once the video edition is available, the playlist will be sited as a pinned comment on the video edition. It is also easy to locate any previous Conference Whispers playlists through TBW Advisors LLC corporate website. Additional cybersecurity conference research is available via Conference Whispers: Identiverse and Conference Whispers: ISC West.
Keynotes and Sessions
Kicking off in dramatic fashion, the conference kicked off with an amazing keynote from non-other than the most famous virus hunters – Mikko Hypponen and father of the Hypponen law of IoT security – one of our favorite coverage spaces. Specifically, Mikko said that if a device is smart, it is vulnerable. It was amazing to hear his story.
On the bleeding edge of things, we received two session summaries from Microsoft’s Thomas Roccia. The first session was his Black Hat session on NOVA – Prompt Pattern Matching regarding a new type of threat gaining traction. The second session is actually at DEFCON – the sister conference where no one would be ignorant enough to bring in modern technology outside of a faraday cage. Fortunately, we caught Thomas while at Black Hat. IN this talk Thomas shared that they are releasing an AI Agent to track crypto currency’s movements including visualization to combat crypto money laundering. The final Microsoft session itself that we captured is the Unmasking of Cyber Villains. I always love when engineers get a very loud boastful ovation from the audience. This stage featured the heroes of MISTIC and Dart who shared how they leverage each other’s strength. MISTIIC stands for Microsoft Threat Intelligence Center while Dart stands for Microsoft’s Diagnostics and Recovery Toolset. In this session, the Microsoft team emphasized that incidents require empathy, speed, and precision. The Darth team is on the ground delivering the empathy and getting the data to MISTIC. MISTIC in turn, provides the cheat codes to the Darth rescue team to quickly combat the incident.
On the topic of using AI Agents on a team of humans in wish SOC, James Spiteri from Elastic Security shared a summary of his session. “AI without Borders: Extending analysts capabilities in a modern Soc” dove into details how Agents and humans can successfully interoperate in a SOC. James also covered critical questions you need to think about in order to truly operationalize this type of situation.
Exhibits
As with many events, some exhibits span outside of the formal expo hall. We were invited to the Dune Security Command Center on site where we heard about their solution. Their adaptive training uses a personal credit risk scoring model. It targets each employee’s risky actions and knowledge gaps with customized, targeted, proactive program. The goal is to elevate them to meet corporate standards. This theme of preparation, training, and doing things up-front was definitely a theme. Cumulated shared how their solution focuses on resiliency. Given that the proper way to discuss it is always when and not if, it is wise to ensure a quick recovery when it occurs. This preparation and looking out for the threat aligned with Qualys’s Risk Operations Center. This center is focused on assisting organization proactively identify, prioritize, and finally remediate identified risks. Covering all five personas in a SOC (alerts, vulnerabilities, threat intel, case management and DFIR (digital forensics/incident response )) StrikeReady’s platform integrates with 800 tools and is focused on removing each role’s pain points. Continuous Threat Exposure Management or CTEM is the area addressed most recently by Safe Security. Booli also moves things earlier in the process, in their case identity stitching. Specifically at the very beginning of the process including score carding the identity and providing the information back to the identity service. Ensuring stolen credentials are changed once they have been phished and the criminals attempted to leverage them, Mokn was on site to tell attendees about their solution.
If your organization would prefer to fix vulnerabilities instead of the common security software composition analysis, Heeler Security was the booth to visit. Feeling overwhelmed, by cloud configurations in your organization? imPac Labs was on site talking about their expertise. Admittedly, given my Microsoft Patent application on Policy Profiles, cloud configurations is a problem space on our radar at TBW Advisors. Speaking of high availability environments, HAProxy Technolog exhibited their platform that brings enterprise security performance and configurability into packaged software.
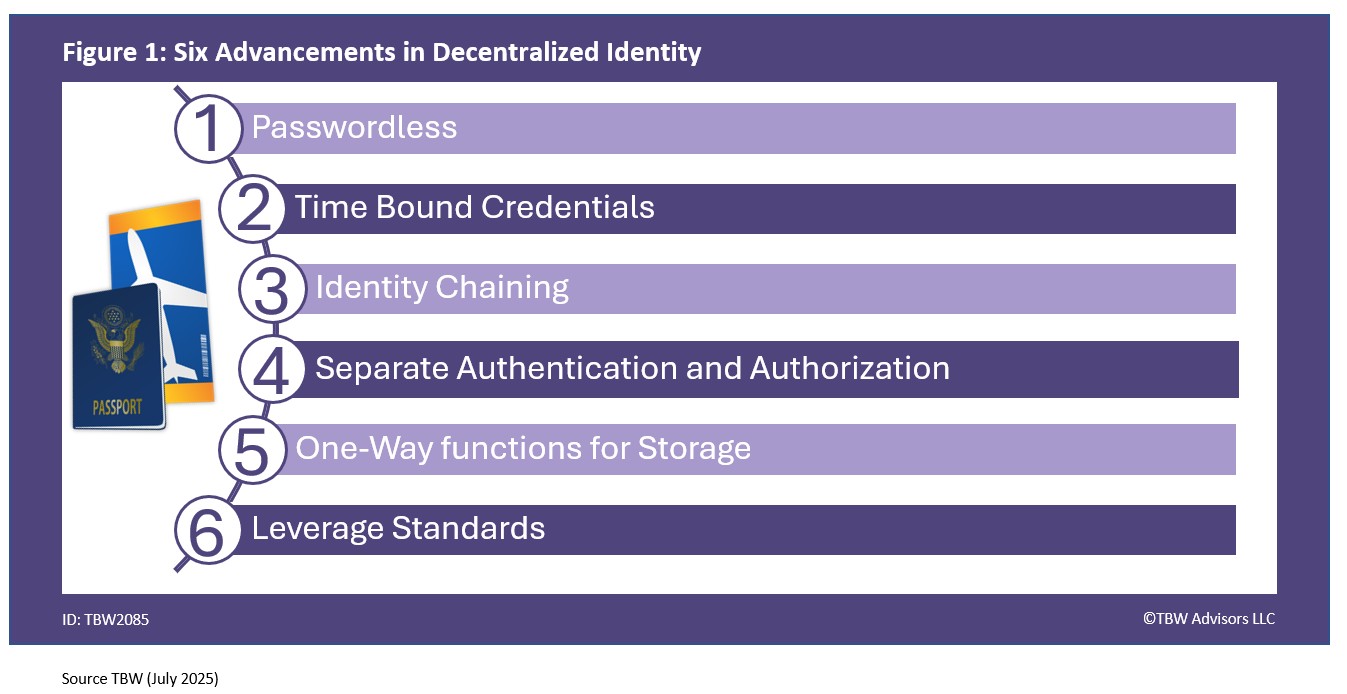
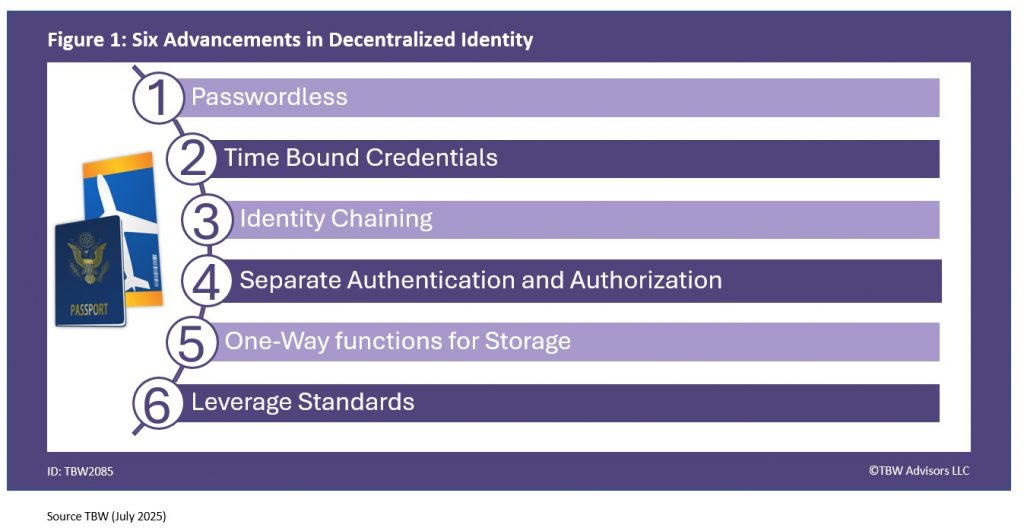
An area we have discussed in Conference Whispers: Money 20/20, Conference Whispers: HIMSS 2025, and Conference Whispers: Fintech Meetup 2025 – verifying the hardware device is a valuable defence vector for fighting fraud. At Black Hat USA 2025 we met SmallStep that enables device identity with cryptographic identity ensuring corporate devices are used to perform work. Leveraging device identification to eliminate deepfakes within a corporation, Netarx leverages multiple models to ensure your corporate communications are safe from deep fakes. Elastic Search – an open-source project known for search – found itself building native security and analytics due to popular demand.
Moving into the agentic side of things, Microsoft’s AI Agent Challenge was a big hit. Their booth had plenty of specialists on site to answer any of your questions. Focusing exclusively on AI Agents for the Red Team, Mindgard’s solution keeps probing to find vulnerabilities, filters through them based on your target and context. Finally, remediation advise is dispensed. Cyata built a built a control plane for Agentic Identity and includes policy enforcement. Addressing the full lifecycle above and beyond triage, Exaforce shared their Agentic SOC Platform. A demo of Exaforce was also captured. Finally, if you are unfamiliar with the current state of agents or have never seen an agent in action, enjoy the video with Ralph. Ralph comes from Cyber Innovate; a think tank focused on stopping threats from AI Agents themselves.
Next Year’s Conference
Black Hat USA 2026 will once again return to Las Vegas and will be held at Mandalay Bay Convention Center in August 2026. The exact dates have yet to be announced at time of publication.
*When vendors’ names are shared as examples in this document, it is to provide a concrete example of what was on display at the conference, not an evaluation or recommendation. Evaluation and recommendation of these vendors are beyond the scope of this specific research document. Other examples products in the same category may have also been on display.

Corporate Headquarters
2884 Grand Helios Way
Henderson, NV 89052
©2019-2025 TBW Advisors LLC. All rights reserved. TBW, Technical Business Whispers, Fact-based research and Advisory, Conference Whispers, Industry Whispers, Email Whispers, The Answer is always in the Whispers, Whisper Reports, Whisper Studies, Whisper Ranking, The Answer is always in the Whispers, and One Change a Month, are trademarks or registered trademarks of TBW Advisors LLC. This publication may not be reproduced or distributed in any form without TBW’s prior written permission. It consists of the opinions of TBW’s research organization which should not be construed as statements of fact. While the information contained in this publication has been obtained from sources believed to be reliable, TBW disclaims all warranties as to the accuracy, completeness or adequacy of such information. TBW does not provide legal or investment advice and its research should not be construed or used as such. Your access and use of this publication are governed by the TBW Usage Policy. TBW research is produced independently by its research organization without influence or input from a third party. For further information, see Fact-based research publications on our website for more details.