Whisper Report: What’s the biggest cybersecurity myth in 2025?
Published to clients: August 19, 2025 ID: TBW2090
Published to Readers: August 20, 2025
Whisper Email Release: TBD
Public and Video Release: TBD
Analyst(s): Dr. Doreen Galli
Photojournalist(s): Dr. Doreen Galli
Abstract:
This Whisper Report identifies eight persistent cybersecurity myths in 2025, from the belief that threats can be fully stopped to misconceptions about AI’s role in security. Experts from Black Hat USA 2025 clarify that resilience, strategic investment, adaptive training, and human oversight remain essential. AI is powerful but not a plug-and-play solution, nor a replacement for human judgment. Understanding these myths helps organizations build more realistic, effective cybersecurity strategies.
What’s the biggest cybersecurity myth in 2025?
We took the most frequently asked and most urgent technology questions straight to the Cybersecurity professionals gathering at Black Hat USA 2025 held in Las Vegas. This Whisper Report addresses the question regarding what’s the biggest cybersecurity myths in 2025? Figure 1 displays the eight cybersecurity myths we uncovered we will now discuss.
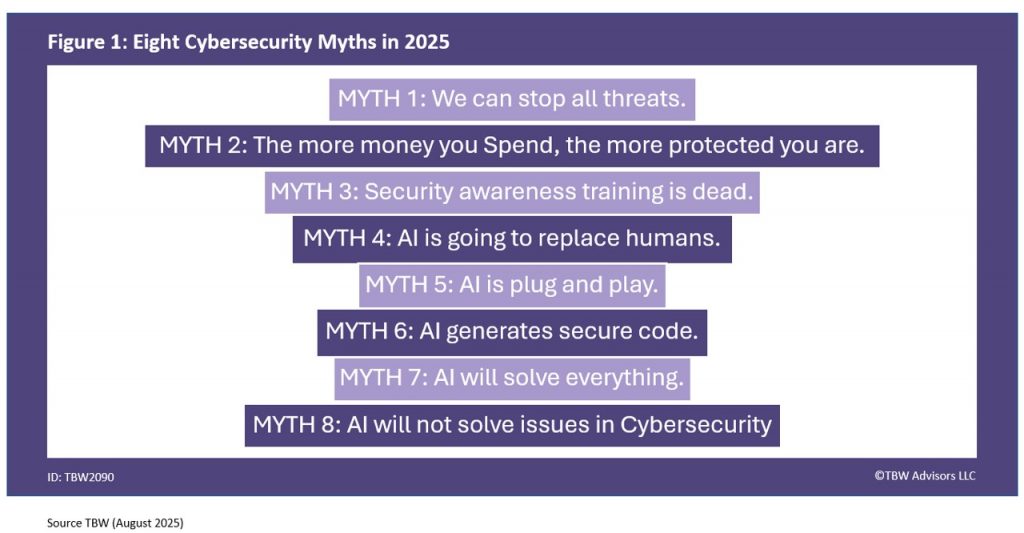
MYTH 1: We can Stop all Threats
The first myth comes from Trustmi’s Corey Sienko and is that “we can stop every single threat from entering the organization” This may come as a surprise to some executives particularly those outside of cybersecurity but the expression used is always when not if you have an incident. No Need to fret, Trustmi’s Corey Sienko continues. “It’s about how do we respond to those threats and make sure that we protect the organization from losing valuable information and cards.” I believe all appreciate that clarification. Cybersecurity involves defense but it is also a game all about preparation for when and resiliency after. This topic is further discussed in Conference Whispers: Black Hat USA 2025.
MYTH 2: The more money you spend the more protected!
Cymulate’s Avihai Ben Yossef brings us myth number two, “The more money you spend on cyber security the more protected you are.” Ben goes on further to explain. “I think in order to really be protected in cyber security from cyber attacks is by actually knowing what you need to do in order to make sure you are protected and when once you know that you don’t need to spend too much money you need to spend you know a very focused amount of money in what matters most.” If you are surprised by this, you really need to book an inquiry with TBW Advisors so we can help you review your cybersecurity strategy. Additional research regarding critical observations on cybersecurity spend can be found in the keynote covered within Conference Whispers: Identiverse 2024.
MYTH 3: Security awareness training is dead!
Cybersecurity Myth number three comes to use from Dune Security’s David DellaPelle. “Security awareness training is improving readiness and reducing risk. Security awareness training is dead.” Intrigued? Let’s hear more from David. “Security awareness training as it exists today, meaning legacy security awareness training technologies are not effective at reducing risk and create friction and an adversarial relationship between the security organization and the end users. The problem is if you think about a doctor who is looking to solve a patient’s problem, the first thing they would do is take in a lot of data and run tests to exclude the possibilities. They quantify the risk before they prescribe a medicine or a surgery. And so if there’s a security awareness training solution that doesn’t automatically provide uh user adaptation, it’s uh it’s kind of falling flat on its face. Every piece of security control or adaptation should be relevant to the individual user’s risk profile and that training or that security measure should be applied automatically based on the risk profile.” Training employees only on what that specific employee personally need to get better at? Sounds optimized.
MYTH 4: AI Is going to replace Humans
Bringing us cybersecurity Myth 4 is StrikeReady’s Alex Lanstein. “AI is going to replace humans.” Alex further clarifi:ed, “AI is always going to augment humans. Anybody who’s ever leveraged any AI system, any generative AI system. You see that it makes mistakes. Sometimes those mistakes are obvious, sometimes they’re subtle. And no one is ever going to turn anything over to an AI when it’s making such obvious or subtle mistakes without a human in the loop.” Or as Elastic Security’s James Spiteri further explained, “we’re thinking about this fully autonomous security operations team. I don’t think that’s going to happen. I don’t think even think it’s the right approach to think about these things. AI and agents are phenomenal, but they are the perfect compliment to humans. They’re not they’re not there to replace humans. They’re there to make humans lives better. eliminate the stuff that humans don’t want to do and let humans do the fun things like make people excited about wanting to work in cyber and that’s what the AI is allowing us to do.”
MYTH 5: AI is plug and play
Brian Mehlman and his AI Agent from Cyber Innovate bring us Myth 5. “I’m actually here with one
of my agents, and his name is Ralph. Ralph, can you answer the question as you see it in our world view? What’s the biggest cyber security myth here in 2025? Absolutely, Brian. Happy to jump in here. So, from our perspective, the biggest cyber security myth of 2025 is probably the idea that AI is just a plug-and-play solution, that it’s kind of a one-size fits-all magic bullet.” Ralph and Brian went on to further explain, “In reality, the myth is that AI will handle everything securely on its own. But the truth is it needs a lot of oversight, a lot of transparency, and people often underestimate the complexity inside the machine. So that’s the big myth that AI is just simple and straightforward when really it’s a lot more nuanced. And that’s my take. Uh I would add my answer. I would extend onto yours is I agree, but um I’m used to systems that have access controls, authentication controls, and audit. Uh inside the black box, we don’t have any of them. Once I log in and I authenticate, it’s a wild wild west. That has to change. Immutable logs within the system is probably something that’s going to happen at some point. Uh or some other unique uh solutions to the problem.”
Interestingly, Ariful Huq from Exaforce observed a similar concern. “Trying to build an LLM wrapper is what I call it without really understanding the data related to the problems that you’re trying to solve. LLMS can only get you so far, right? They are large language models and summarization and contextualization but at the end of the day if you want to solve problems related to say detections investigations LLMS can only get you so far right you really need to go back to the data go back to the fundamentals and then layer on a large language model on top of it to solve some of the problems that around like you know summarization um you know building agent workflows.” In other words, solutions are custom crafted – NOT plug and play.
MYTH 6: AI Generates secure code
Checkmarx’s Jonathan Rende brings us Myth 6, “AI generates secure code.” That myth should grab the attention all organizations leveraging coding agents to quickly advance their product. Jonathon continues, “It doesn’t. It doesn’t. And it will probably get better over time. And will it do a better job than a junior developer in simple mistakes that can cause vulnerabilities? Heck yeah, of course it will. But for the more complex issues, it’s not there yet. AI is not there yet.”
MYTH 7: AI will solve Everything
Let’s hear Myth 7 from Booli’s Joe Schorr, “the biggest cyber security uh myth is that AI is actually going to solve everything.” Joe went on to further explain, “I think if you judiciously apply AI, machine learning and very discreet task and things, it’s fantastic. I think it’s being overblown quite a bit right up at the myth level. I think that if you treat it like we treat it in Booli, we’ve got AI built in, but we don’t publish it all over everything we’ve got, but we treat it kind of like an idiot savant. It’s it does one to ask really well or does a discrete set to ask really well. It may not actually behave well in church, but you can get it to do what you want for something very very specific, which is how we do it. I think the myth is that AI is going to solve everybody’s problems.” Brian Sledge of imPAC also believes that AI will solve everything is a myth. “I think AIis best positioned more like a forcemultiplier, but I don’t think it solvesthe problems, the core problems of cybersecurity today. Um cyber security stillrequires context. It requirespolicy driven control and those thingsstill require human in the loop. And Ithink the best way to leverage AI isn’t so much in solving for cyber security,but it’s more for helping multiply andscale out what humans still need andwe’re required to do. So I don’t think Idon’t think customers should sleep onthe idea that humans still need to be very much engaged as part of cyber security. Because cyber security AIis only as good as the algorithms andthe models and the data it’s getting.” Thus believing in 2025 AI will solve everything is a stretch but will it solve something?
MYTH 8: AI Will Not Solve Issues in Cyber Security
Microsoft’s Thomas Roccia brings us Myth 8. “right now I think most people in in the industry in the security industry doesn’t yet believe in this technology (AI) and that’s maybe one of the one of the myths that AI will not really solve issue in cyber security. We have and I think that’s a mistake it’s probably something which is changing the way we are doing and all the past work that we did for the past 20 or 30 years uh is going to be changing and evolving thanks or because to AI so that’s something to consider.” Thus, while it may not solve everything today, it is changing how the industry works and what it is fighting against.
*When vendors’ names are shared as examples in this document, it is to provide a concrete example of what was on display at the conference, not an evaluation or recommendation. Evaluation and recommendation of these vendors are beyond the scope of this specific research document. Other examples products in the same category may have also been on display.
Related playlists and Publications
- Conference Whispers: Black Hat USA 2025
- Conference Whispers: Identiverse 2024.
- Conference Whispers: Identiverse 2025
- Whisper Report: What’s the biggest cybersecurity myth in 2025.
Corporate Headquarters
2884 Grand Helios Way
Henderson, NV 89052
©2019-2025 TBW Advisors LLC. All rights reserved. TBW, Technical Business Whispers, Fact-based research and Advisory, Conference Whispers, Industry Whispers, Email Whispers, The Answer is always in the Whispers, Whisper Reports, Whisper Studies, Whisper Ranking, The Answer is always in the Whispers, and One Change a Month, are trademarks or registered trademarks of TBW Advisors LLC. This publication may not be reproduced or distributed in any form without TBW’s prior written permission. It consists of the opinions of TBW’s research organization which should not be construed as statements of fact. While the information contained in this publication has been obtained from sources believed to be reliable, TBW disclaims all warranties as to the accuracy, completeness or adequacy of such information. TBW does not provide legal or investment advice and its research should not be construed or used as such. Your access and use of this publication are governed by the TBW Usage Policy. TBW research is produced independently by its research organization without influence or input from a third party. For further information, see Fact-based research publications on our website for more details.