Published to clients: July 30, 2025 ID: 2085
Published to Readers: July 31, 2025
Whisper Club: December 15, 2025
Public: January 20, 2026
Analyst(s): Dr. Doreen Galli
Photojournalist(s): Dr. Doreen Galli
Abstract:
“Recent advancements in decentralized identity include passwordless authentication, time-bound credentials, and dynamic identity chaining. These innovations reduce risk, improve privacy, and enhance user control. Separation of authentication from authorization enables more precise access management. One-way functions protect biometric data in cloud environments. Emerging standards like SPIFFE and CSA’s agentic identity frameworks offer scalable, interoperable solutions. Together, these developments support secure, flexible identity ecosystems without relying on centralized authorities.”
Computer Talk Radio coverage of document.
Target Audience Titles:
- Chief Information Security Officer, Chief Technology Officer, Chief Digital Officer, Chief Privacy Officer, Chief Product Officer, Chief Data Officer
- Identity and Access Management Engineers, Security Architects, Cloud Infrastructure Engineers
- Privacy Engineers, Standards and Compliance Analysts
Key Takeaways
- Passwordless authentication removes friction and improves security.
- Time-bound credentials limit exposure from compromised access.
- Identity chaining enables dynamic, temporary access provisioning.
- Authentication and authorization are increasingly separated for clarity and control.
What are the latest advancements in decentralized identity and verifiable credentials?
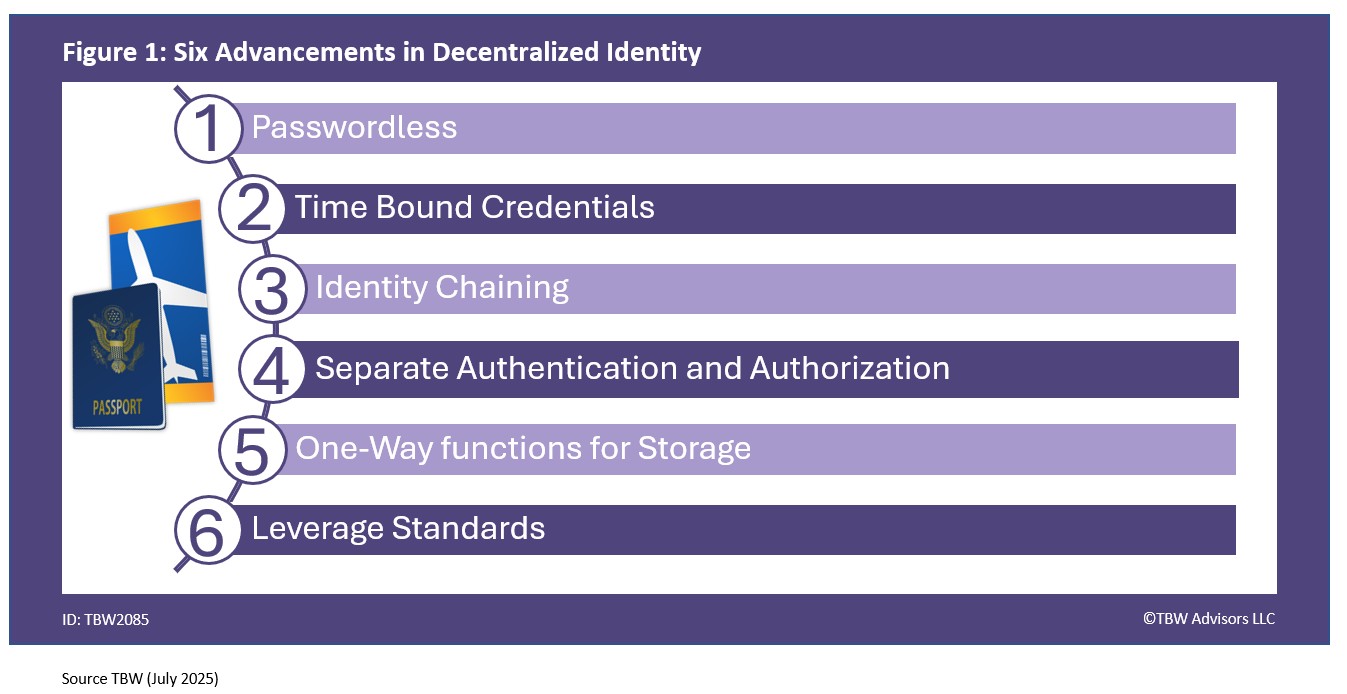
We took the most frequently asked and most urgent technology questions straight to the Technologists gathering at Identiverse 2025 held at Mandalay Bay in Las Vegas. This Whisper Report addresses the question regarding the latest advancements in decentralized identity and verifiable credentials. But what is a decentralized identity. Panini’s Jim Harris explained, “identity – being able to capture that information using nearfield technology and then verifying that issue issuing information with the agency that issue it to certify that customer is legitimately who they say they are so we believe that’s one of the ways we can support authentication in a digital decentralized environment.” Let’s dive into six advancements in decentralized identity for you to add to your environment as depicted in Figure 1.
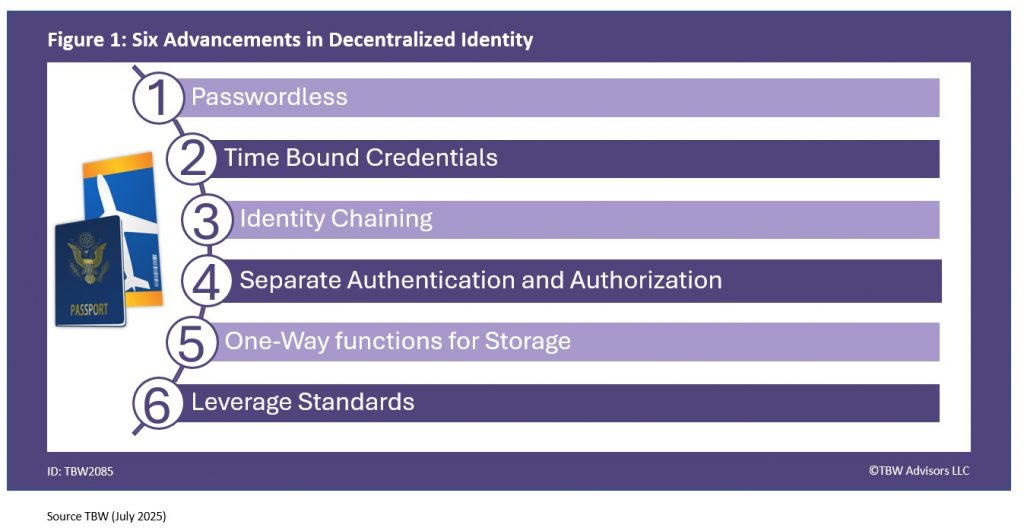
1. Passwordless
Frequently involved in moving authentication from something you know to something you are, Passwordless takes those pesty passwords out of the equation. As Simeio’s Octavio Lopez observed, “I’ve been seeing a lot of a lot of organizations are pushing towards passwordless.” For vendor examples that provide biometric identity options see Conference Whispers: Identiverse 2025 and Conference Whispers: ISC West 2025.
2. Time Bound Credentials
A favorite tactic to limit any damage from stolen credentials is to time bound them. As GitGuardian’s Dwayne McDaniel explained, “How do we not store a long-term credential but instead expose only the bit of the credential you need to verify that entity should be doing that thing and then issue a very short live jot or 509 Cert (X.509 certificate) that will expire immediately.” Any compromised short-lived credential is useless thereby limiting the blast radius in the system.
3. Identity Chaining
Related to time bound credentials is the dynamic identity chaining. As Apono’s Ofir Stein revealed the key to decentralization of identities is, “it’s the ability to create dynamic changes in the identity that exist in the environment. Meaning by that we keep what we call identity chaining while if I need access to some resources let’s say in cloud we create all the identities that needed for me to work and then we revoke them so dynamic approach to decentralized identity in a panel the dynamic approach is the decentralized identity when we create identity when needed and we work them when they when they don’t need them.”
4. Separation Authentication and Authorization
“Although commonly associated together, as the namespace identity and access management imply, the decentralized identity world is seeing a separation. Authentication — the verification you are who you say you are — is being distinguished from authorization — the granting of some authority to some resource. As GitGuardian’s Dwayne McDaniel highlighted, “we’re going to see some major advancements with this idea of I can prove on me but that doesn’t automatically authorize me for things the authorization is starting to be separated from authentication in a way that should have probably done in the first place.”
5.One-way Functions for Storage
As one might suspect, many identity solutions involve the cloud. The concern becomes, how to store the data in such a way that even if the data stored is compromised – the identity information is not? Keyless’ Alex Jones elaborated on the use case. “when you’re talking about privacy in the biometric space it’s all about where your biometric data goes does it stay on the device does it stay on the cloud so within cloud-based biometrics which is what Keyless does, there’s different ways of making sure that the biometric data on the cloud is kept really safe and this is where a decentralized biometric system come in it’s basically transforming the biometric data when it goes on the cloud so that when it’s there it is completely unrecognizable so even if the cloud server is compromised the biometric data or the data that’s stored there is kept safe.” This is the same approach we saw leveraged during our coverage of ISC West. A hash of the data is stored not the data itself. This hash function can be used against new data presented to see if the two results match properly. There is no reverse of this hash function thus the original data cannot be disclosed even if the resulting hash is compromised.
6. Leverage Standards
Finally, when you are creating your roadmap or architecture you do not have to reinvent the wheel. As GitGuardian’s Dwayne McDaniel denoted, “we’re seeing the standards emerge right now about 7 years ago we saw SPIFFE the secure production identity framework for everyone emerge and that came out of what Google was doing internally. Number of working group that sprung up at Netflix and they wrote a beautiful book on it called solving the bottom turtle. The CSA has just put out a new paper May 25th on how dissolve this multi- agent system problem and introducing concepts like agentic name spacing and a distributed ID like as name spaces and it’s just a fascinating time now.”
Final note
For those wishing to see a case study about how to bring a massive, decentralized identity solution to life, Identiverse had a keynote for you. Specifically, a case study of the UK mobile identity deployment featuring Hannah Rutter, Deputy Director, Digital Identity of the United Kingdom. If your organization is on the decentralized identity path, there is no reason to go alone. Reduce the risk and increase your chances of success by working with TBW Advisors LLC. Schedule an inquiry at the beginning of the process and each critical step to stop missteps.
Analysis available only to clients at this time. Join the YouTube Whisper Club at the Whisper Club Level to get access to the video edition today.
Related playlists & References
- Whisper Report: How can organizations implement zero-trust security without disrupting user experience?
- Conference Whispers: Identiverse 2025
- Conference Whispers: Identiverse
- UK Identity Case Study Keynote
- CSA’s Publication, “Agentic AI Identity and Access Management: A New Approach”
- Conference Whispers: ISC West 2025
- SPIFFE
Corporate Headquarters
2884 Grand Helios Way
Henderson, NV 89052
©2019-2026 TBW Advisors LLC. All rights reserved. TBW, Technical Business Whispers, Fact-based research and Advisory, Conference Whispers, Industry Whispers, Email Whispers, Whisper Club, Whispers, The Answer is always in the Whispers, Whisper Reports, Whisper Studies, Whisper Ranking, The Answer is always in the Whispers, and One Change a Month, are trademarks or registered trademarks of TBW Advisors LLC. This publication may not be reproduced or distributed in any form without TBW’s prior written permission. It consists of the opinions of TBW’s research organization which should not be construed as statements of fact. While the information contained in this publication has been obtained from sources believed to be reliable, TBW disclaims all warranties as to the accuracy, completeness or adequacy of such information. TBW does not provide legal or investment advice and its research should not be construed or used as such. Your access and use of this publication are governed by the TBW Usage Policy. TBW research is produced independently by its research organization without influence or input from a third party. For further information, see Fact-based research publications on our website for more details.